Intrusion Prevention
Intrusion prevention (also known as tarpitting) allows you to block any IP address performing suspicious activities.
This option serves e.g.: as protection against spammers who are trying to spam your IceWarp Server accounts based on email address dictionary attacks or DoS (Denial of Service) ones.
Most of these rules do not affect authenticated users, except # of connections per minute and RSET (since authentication is lost when RSET command is sent).
There is an option to create a "bypass list" of IP addresses which will never be blocked.
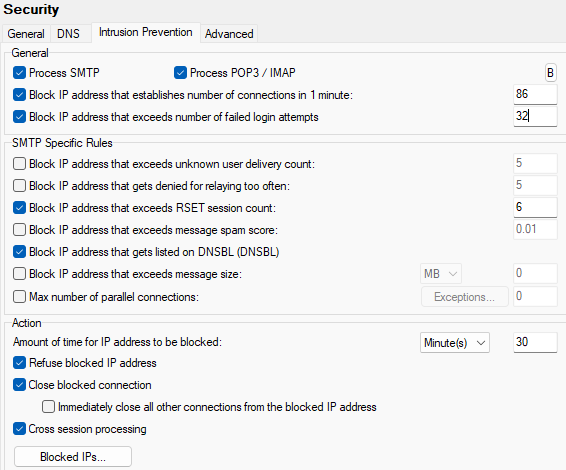
Figure. Security level management: Intrusion Prevention tab.
General section
|
Field |
Description |
|---|---|
|
Process SMTP |
Enables the feature for SMTP. |
|
Process POP3/IMAP |
Enables the feature for POP3/IMAP. Supported options are limited to ones included in the General section. |
|
"B' (Bypass) button |
Click the button to edit the standard Bypass file. Note: Several of the conditions are evaluated in early stage of the SMTP session, when not enough information about the session is present. e.g.:: The Local Sender condition can not bypass Block IP address that exceeded number of failed login attempts, because a sender is not known when authentication is done. |
|
Block IP address that establishes number of connections in 1 minute |
Check this option and specify a value. In the above example an IP address that establishes 86 (or more) connections in one minute will be automatically blocked. |
|
Block IP address that exceeded number of failed login attempts |
IP address will be added to blocked list after unsuccessful login attempt which exceeds the number of failed attempts specified. |
SMTP Specific rules section
|
Field |
Description |
|---|---|
|
Block IP address that exceeds unknown user delivery count |
Check this option and specify a value. When activated, the server will monitor all suspicious activities. If the number of activities from one server exceeds the threshold setting, this IP address will be blocked (denied access) for a specified amount of time. In the above screenshot, an address will be blocked after it attempts to deliver 5 messages to unknown users. |
|
Block IP address that gets denied for relaying too often |
Check this option to automatically block addresses that attempt to relay through IceWarp Server more than the number of times specified. |
|
Block IP address that exceeds RSET session count |
Check this option and specify a value. In the above example any connection that issues more than 5 RSET commands in one session will be blocked. |
|
Block IP address that exceeds message spam score |
Check this option and specify a value. In the above example any IP address that delivers a message with a spam score higher than 5.5 will be automatically blocked. |
|
Block IP address that gets listed on DNSBL |
Check this option and any connection that is refused because it is on a DNSBL will also be blocked. |
|
Block IP address that exceeds message size |
Check this option to have the IP address blocked for any connection that attempts to deliver a message greater than the specified size. Specify a value and choose Kilobytes, Megabytes or Gigabytes from the dropdown box. |
|
Max number of parallel connections |
If the number of connections coming from a particular IP address exceeds the limit set here, no more SMTP connections are accepted. (This value is related to the MailServer.ParallelIPConnectionsLimit variable. Zero means no limit.) Click the button to specify an IP address (or a range of IP addresses) where this limit is not applied. |
Note: This check differs from the standard SMTP "maximum
message size" check in that the connection is closed as
soon as the size threshold is reached and the IP address blocked.
This is useful for stopping potential bandwidth abusers who send large
messages.
For example with the settings shown above, someone sends
a 1GB message to one of your users. As soon as the system has received the
first 100MB it will close the connection and block the IP address for 30
minutes. The sending SMTP server may try to re-send the message but it
will be denied access until these 30 minutes are up, at which point the
first 100MB will be accepted then the block happens again. Eventually the
sending SMTP server will give up trying to send the message.
The effect on your server is that instead of having a
high bandwidth usage for a 1GB duration it will have high bandwidth usage
every 30 minutes for a 100MB duration until the sending server gives up,
freeing your bandwidth for other send/receive operations in the
meantime.
Action section
| Field |
Description |
|---|---|
|
Amount of time for IP address to be blocked |
Specify here how many minutes (hours, days) an IP address should be blocked for. |
|
Refuse blocked IP address |
Checking this option will store the blocked IP in a database and refuse any further connection attempts. Note: It is meaningful (and recommended) to have checked at least one of following options: Refuse blocked IP address, Close blocked connection. |
|
Close blocked connection |
Check this option if you want to have closed immediately all intrusive connections from an IP address that has just been blocked. Other current connections from this IP are not closed. All connections just incoming from this IP address are blocked for the time specified in the Amount of time ... field. |
|
Close all other connections from the blocked IP immediately |
Check this option if you want to have closed immediately all other intrusive connections from an IP address that has just been blocked. |
|
Cross session processing |
Check this option IceWarp Server to collect Intrusion Prevention stats across multiple sessions (connections) from the same server. Stats are accumulated over the time selected in Amount of time for IP address to be blocked. In the above example, connections from HostA would be collected and acted upon for 30 minutes. There are some cases where using of this option is senseless. e.g.: Block IP address that exceeds message spam score, Block IP address that gets listed on DNSBL, Block IP address that exceeds message size. Contrary, the Block IP address that establishes number of connections in 1 minute option performs Cross session processing automatically. |
|
Blocked IPs |
Press this button to jump to the Intrusion Prevention queue, where you can manage blocked IP addresses. |
Intrusion Prevention Reason Codes
| Reason Code |
Explanation |
|---|---|
|
C |
Tarpitting invoked via Content Filters |
|
I |
IP blocked for exceeding connections in one minute |
|
M |
IP blocked for delivering oversized message |
|
R |
IP blocked for exceeding RSET command count |
|
D |
IP blocked for being listed on DNSBL |
|
A |
The account that this message was sent to was a "tarpit" account so the sending IP is tarpitted |
|
P |
IP blocked for exceeding unknown user delivery count |
|
Y |
IP blocked for relaying |
|
S |
IP blocked for exceeding spam score in a message |
|
U |
IP blocked manually via IceWarp Server's console |
|
L |
IP blocked for too many failed login attempts |

