DNS
DNSBL is a DNS server which only lists IP addresses of known spammers.
If you query an address against a DNSBL server and get a positive result, the address is most likely of a known spammer.
This can be used as an Antispam technique.
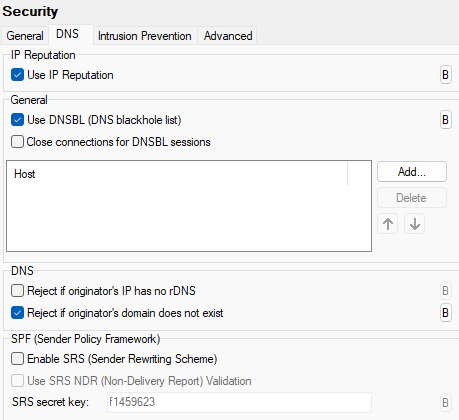
Figure. Security management: DNS tab.
IP Reputation section
General section.
DNS section
SPF (Sender Policy Framework) section
|
Field |
Description |
|---|---|
|
Enable SRS (Sender Rewriting Scheme) |
Activates the SRS technology fixing the SPF forwarding mail issue, by forcing the agent to change the "mail from" address. Note: When using SRS, it builds the MAIL FROM always referring to the primary domain. You may have a reason not to show your primary domain but still use this feature. The solution is to have SRS enabled + enable the Use domain IP address for outgoing connection feature (Domains and Accounts > Global Settings > Domains > Other) or set the C_Accounts_Global_Domains_IPAddress API variable to 1. |
|
Use SRS NDR (Non-Delivery Report) Validation |
Activate this feature if you want the server to validate whether incoming NDRs (bounce backs) contain the correct SRS hash (see SRS secret key). If not, these NDRs are not delivered into users' mail boxes. |
|
SRS secret key |
The secret key is any arbitrary string you can make up - it is your own pass phrase. The secret key will be used for ciphering the data (for hash creation). This field must not be left blank. |
|
'B' button |
Use to open and edit the SRS bypass file - srsbypass.dat. See the example in the bypass file for the correct syntax. |

