WebAdmin
IceWarp WebAdmin is the web-based interface for IceWarp Server administration.
Please be aware of its limitations compared to other administrative tools:
- WebAdmin cannot execute programs, stop Web/Control service without disconnecting you, it provides only basic charting/statistics and some advanced setup options are not implemented.
For comprehensive remote server management, consider the following tools:
- Remote Connection from Administration GUI application, more details in Remote Server Administration.
- Administration GUI including Remote Console also runs in Wine on Linux. More details can be found in the Linux Quick Guide and in Support Knowledge Base.
- The command line interpreter tool.exe or tool.sh for direct API access, more details in the IceWarp Server API chapter.
- Linux wizard script ./wizard.sh which provides basic operations on account, storage and license management. More details in Installation and Control in Linux guide.
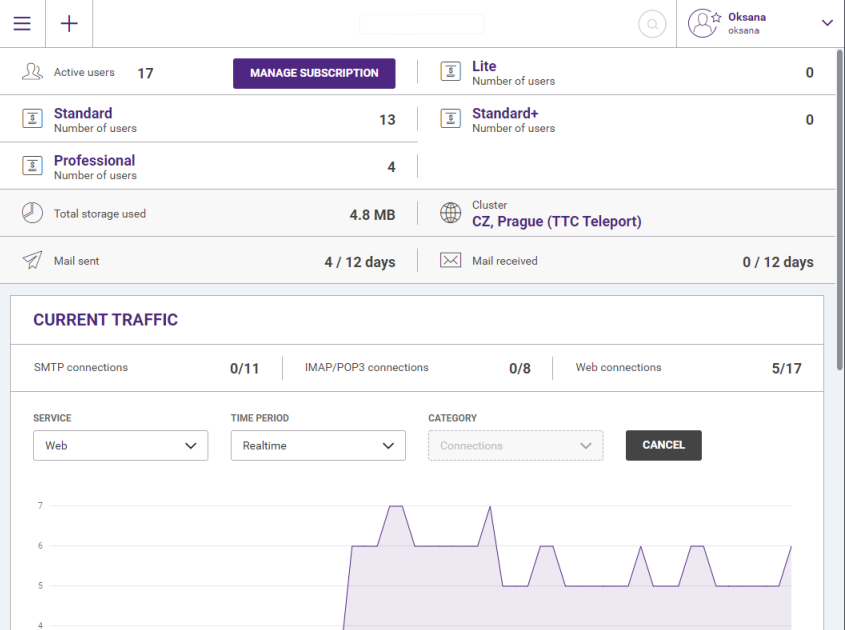
Figure. WebAdmin main view.
Working with WebAdmin is very comfortable because the design of the options was developed to be easy to use for both novices and professionals.
You can access WebAdmin at:
- http://<yourIP>/admin/
If you don't use the default port:
- http://yourIP[:ControlServicePort]/admin/
- http://hostname/admin/
- http://hostname[:ControlServicePort]/admin
Example:
If you are running the Control service on the default port 80 and you have your server installed on a computer with IP address 83.21.14.51 you can access WebAdmin at http://83.21.14.51/admin/
Figure. WebAdmin logon screen.
Additionally, you can set a new web service host on your IceWarp Server to access the WebAdmin at a defined URL, e.g.: http://webadmin.yourdomain.com. You should create such a host also in your DNS pointing to your IceWarp Server's IP and in the website definition, in the Web node of the console, set the home directory to html\admin.
WebAdmin respects the extended access rights that you can specify in Main Menu. This way you can limit access of domain administrators to only specified domains, set which particular account types the administrator can modify and hide administrative options they should not be able to access.

