SSL Tunnel
An TCP/IP tunnel is a gateway listening on a specific port that forwards all communications to a specific destination.
IceWarp Server allows you to create multiple TCP/IP tunnels on your system, which can optionally be SSL encrypted.
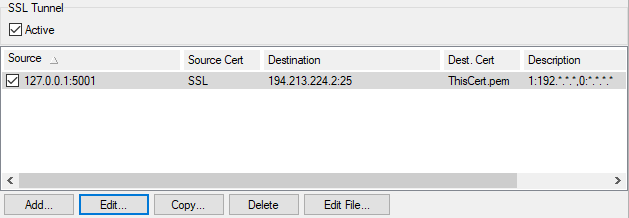
Figure. Tool management: SSL Tunnel.
|
Field |
Description |
|---|---|
|
Active |
Check the box to activate the service. Removed in new version? |
|
Source |
Shows the listening IP address and port. |
|
Source Cert |
Shows whether the connection to the tunnel should be SSL encrypted and whether a certificate should be used. |
|
Destination |
Shows the destination of the tunnel. |
|
Description |
A free-form field where you can describe this tunnel. |
|
Active |
Shows whether this tunnel is currently usable. |
|
Add |
Click the button to define a new tunnel. The SSL Tunnel dialog opens. |
|
Edit |
Select a tunnel and click the button to edit this tunnel. The SSL Tunnel dialog opens. |
|
Copy |
Select a tunnel and click the button to copy this tunnel. The SSL Tunnel dialog opens. Useful when creating a similar tunnel. |
|
Delete |
Select a tunnel and click the button to remove this tunnel. |
|
Edit File |
Opens a plain text editor showing the tunnel definitions file content. Syntax and examples are given in the file. |
SSL Tunnel Dialog
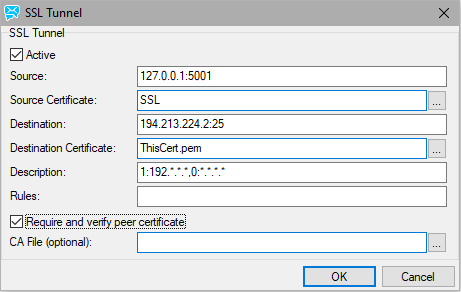
Figure. SSL Tunnel dialog.
|
Field |
Description |
|---|---|
|
Active |
Check the box to have this tunnel active. |
|
Source |
Where IceWarp Server will listen. Syntax: [IP]:port IP - optional, the listening IP address :port - mandatory, the listening port
Examples: :5001;SSL Listens on all interfaces on port 5001 as an SSL server 127.0.0.1:5001 Listens on IP 127.0.0.1 port 5001 |
|
Source Certificate |
Use this field to specify whether the connection to the tunnel should be SSL encrypted and whether a certificate should be used.
|
|
Destination |
Where IceWarp Server will send received data. Syntax: [IP]:port IP - optional, the IP address :port - mandatory, the port
Examples: gate.icewarpdemo.com:80 Sends data to gate.icewarpdemo.com port 80 194.213.224.2:25 sends data to 194.213.224.2:25 port 25 |
|
Destination Certificate |
Use this field to specify whether the connection to the tunnel destination should be SSL encrypted and whether a certificate should be used.
|
|
Description |
Enter a free-form text description so you can easily identify this tunnel. |
|
Rules |
Here you can specify rules as to which IP addresses are allowed to establish incoming connections. Syntax: [Rights]:[IP Range];[Rights]:[IP Range] Rights1 to allow, 0 to deny IP Range - IP address or mask Examples: >1:192.*.*.*;0:*.*.*.* >Allows connections only from 192.*.*.* >0:192.068.6.* >Deny connections from 192.068.6.* Note: Using of these rules is not recommended. We recommend to use certificates to control access. |
|
Require and verify Peer Certificate |
Check this box to force all connections for this tunnel to have a peer certificate. Any connection that does not supply a certificate will be dropped. Any connection that connects with SSL but has no certificate will be dropped. If a certificate is supplied, it will be checked against the CA file specified in the next field. If no CA file is specified, the file defined in CA Certificates will be used for verification. |
|
CA file (optional) |
You can enter a path to a specific certificate file here if you need to. This can be useful if you want to use a highly secure certificate for certain protocols or tunnels. |

