General
The General tab allows you set messages delivery.
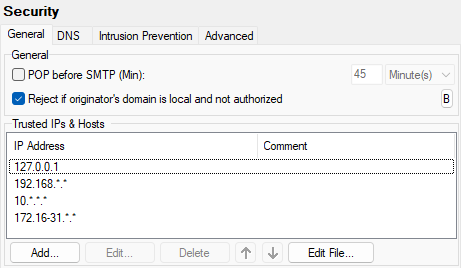
Figure. Security management: General tab.
|
Field |
Description |
|---|---|
|
POP before SMTP (Min) |
Check this option and a local email address which has made a successfully authenticated POP or IMAP connection will be allowed (for specified number of minutes) to initialize SMTP session (from the same IP address which was used for the POP or IMAP connection) with the same rights as if it was successfully SMTP authenticated. |
|
Reject if originator's domain is local and not authorized |
If the sender of the message is a local user (claims to be from your local domain), they have to authorize themselves. Authorization can be done using the SMTP authentication, relaying from IP address or the POP before SMTP feature. This option can reject also local users if they authenticate against different SMTP server, e.g.: their ISP SMTP server. Note: Whitelist and blacklist are skipped if the remote side tells us the sender is local, but the session is not authenticated nor comes from a trusted IP. The email is then processed as usually - other rules are applied. It can be turned off only using API Console - the SpamSkipBypassLocalUntrusted variable. Bypass reason code - H. For more information about reason codes, refer to the Reason Codes. Note: This option can cause problems if user is in a place where internet access is offered (e.g.: hotels) that forces their SMTP to users. |
|
Add |
Click the button to add a new IP address. The IP Address dialog opens. CIDR notation/ranges can be used. |
|
Edit |
Select an IP address and click the button to edit this address. The IP Address dialog opens. |
|
Arrows |
Use the buttons to move addresses up or down in the list. |
|
Edit File |
Click the button to open the simple text file containing the IP ranges. Examples are given there. |
The Trusted IPs list shows the IP address ranges you consider trustworthy. SMTP connections from these IP addresses will be allowed without authentication. For this condition is necessary to have "Whitelist trusted IPs and authenticated sessions" checkbox ticked in Antispam > White & Black List > Whitelist > Advanced.
Note: This list of trusted IPs is also used by the Antispam engine's whitelist as a bypass list,0 if the Whitelist trusted IPs and authenticated sessions option is checked in Antispam > White & Black List > Whitelist .
IP Address Dialog
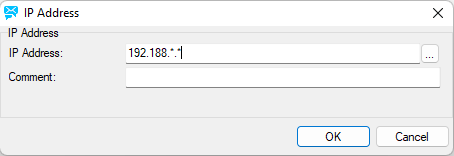
Figure. General tab: IP Address dialog.
|
Field |
Description |
|---|---|
|
IP Address |
Fill in an IP address. You can use masks, as shown above, and ranges, for example: 192.168.0.1-50 Note: You can use host names as well as IP addresses. |
Submission Port (RFC4409)
This port is used as a way to avoid SMTP abuse. Users are forced to use port 587 that requires authentication. In this case, the standard port 25 is used only for communication that is not authenticated (between SMTP servers). It means that all possible spam attempts etc. go via antispam and antivirus filters/rules set on the server for unauthenticated communication.
If you want to use this feature:
-
Enable SMTP AUTH via API:
tool modify system c_mail_smtp_delivery_messagesubmission 1
-
Inform users to change their email clients to use port 587 for SMTP.
-
Check whether the SMTP service has set the 2nd basic service field set to 587. (System - Services - General - SMTP dialog - Properties tab). If not, change it - it works only if set as 2nd basic!
Warning: Since WebClient requires authentication by default, it is also necessary to change the port in the SMTP Server field (Console - WebClient - General).
e.g.: mail.icewarpdemo.com:587.
The same applies to EAS and Spam reports.
Note: Submission port (if enabled via API) PERMITS MAIL FROM account@localdomain.com (where localdomain.com is created on the IceWarp Server where submission port is enabled).
But it still REJECTS due to submission if MAIL FROM is xxx@localdomain.com where xxx is an account that doesnt exist in the local domain. Then the submission bypass is required.
Submission Port Bypass
You may want to bypass the submission port for local users (when MAIL FROM is local). In this case, do the following:
-
Create the submissionbypass.dat file.
-
Use the standard bypass file syntax - "l:" - as for Local Sender.
-
Save this file into the <install_dir>/Config/ directory.
Submission Username and Password
You can also use two variables - <smtp_user> and <smtp_pass> - for unauthenticated operations (e.g.: on login screen, in reports, etc.) to authenticate to SMTP. In this case, add these variables (tags) into the server.xml file (<install_dir>/config/_webmail).
Use credentials of the account that will be used for SMTP authentication by WebClient in the case a user is not logged in.
Another way how to deal with such operations is to add localhost or 127.0.0.1 to trusted hosts (default settings) - SMTP will not require authentication.

