Directory Service
This option allows you to have IceWarp Server synchronized with directory service via LDAP protocol.
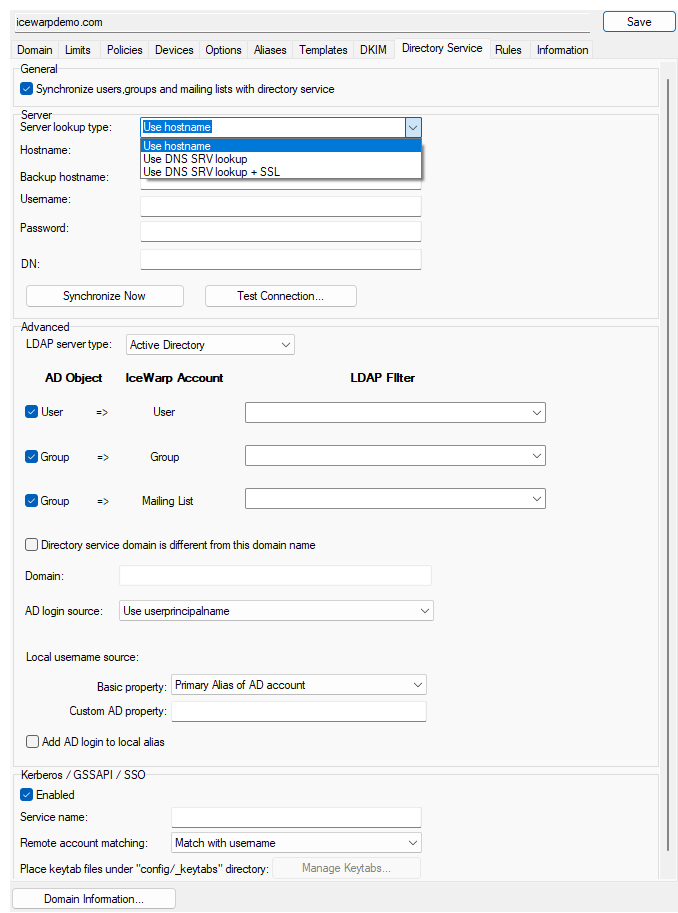
Figure. Domain level management: Directory Service tab.
It supports Active Directory (AD) or other kinds of LDAP directory servers. However, we recommend using LDAP server that supports operational attributes modifyTimestamp and entryUUID. For instance, you may use OpenLDAP. IceWarp Server uses those attributes to identify entity even after email address is changed or to detect change of user data. If you don't use these two attributes, the only way to identify the entity is to use an email. In this case IceWarp Server process all user data on each synchronization. This can cause serious performance problems. In order to avoid it, you need to disable synchronization of groupware (user) data. Go to File > API console, set c_system_adsyncdisablevcardsync API variable to true.
IceWarp Server synchronizes on a regular basis. This means that if you make any changes to user data within the directory server, they will be reflected on IceWarp Server. However, there is a limitation. IceWarp Server stores most of user properties into its vCard, which are handled by groupware. If you change vCard on IceWarp Server side, the change will not be saved during synchronization. It happens because the attributes in LDIF are not stored in IceWarp Server for the changed entity.
Synchronization is done every five minutes by default. If you want to change the time, go to File > API console and set new value in the c_accounts_global_activedirectorysyncinterval API variable.
Note: Only one-way synchronization is possible. Directory
server pushes changes to IceWarp Server. If you change user data within IceWarp Server ,
this change will not be reflected on the directory server and IceWarp Server will revert this change to match the state on the directory server. But you can still create users within the domain which do not exist on your
directory server. Such users will not be affected by the synchronization
engine.
Exception: There is a way how users synchronized against
a directory server can change their passwords via IceWarp WebClient. This
option is available for Active Directory and IceWarp Server version 10.3.0 and newer,
for generic LDAP servers version 11.2.0 and newer. For more information, refer to the Changing Password via IceWarp WebClient.
User template will be applied on newly created IceWarp accounts since version 11.3.0.
General section
The option "Synchronize users and groups with directory service" is available only for products with Cisco Integration enabled. Also when external synchronization library is presented in dedicated folder - {install_path}/externalsync. Check the checkbox to allow synchronization of users and groups with an Active Directory or other LDAP server.
Figure. Directory Service tab: General section.
Server section
In this section you can specify the details of the directory server.
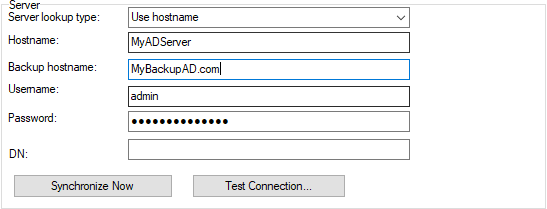
Figure. Directory Service tab: Server section
Advanced section
In this section you can specify advanced settings of the directory server.
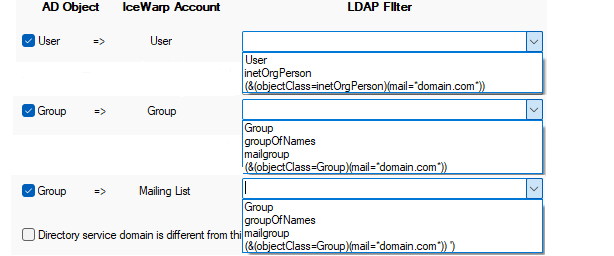
Figure. Directory Service tab: Advanced section.
Figure. Directory Service tab: Advanced section.
|
Field |
Description |
|---|---|
|
Directory service domain is different from this domain name |
Check this option in the following cases:
See the The domain names of your directory server and IceWarp Server do not match and Email Domain of AD Accounts Is Different from IceWarp Server Domain. |
|
Domain |
If your LDAP domain name is different from your
IceWarp Server domain name, you should specify it here. You can also specify a second AD domain name here, separated with a semicolon, if required. Ask your AD administrator whether it is necessary.
Example 2:
Example 3:
See the The domain names of your directory server and IceWarp Server do not match and Email Domain of AD Accounts Is Different from IceWarp Server Domain. |
|
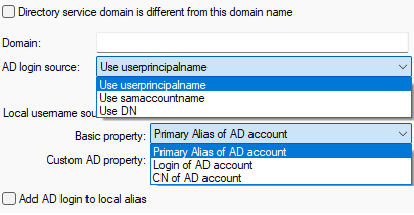
AD login source |
Select which property is used as a source of login by onto your directory server. This setting controls what is put into the u_authmodevalue variable of a synchronized user:
|
|
Local username source, Basic property |
This setting determines which LDIF attribute will be used by the IceWarp Server as username for IceWarp provided services:
|
|
Local username source,Custom AD property |
Set a custom LDIF attribute that you want to use as a source for username of accounts in IceWarp Server. Setting a value into this field will override and disable what you set in the Basic property dropdown. This field displays content of the USERNAMEFROMSPECIALFIELD element of the syncad.dat config file. For instance, if you wish to use LDIF attribute description as username in IceWarp Server, type description into this input. |
|
Add AD login to local alias |
Check this box if you want the user's AD login name to be added to the Alias field within the Management > {domain} > {user} > User. AD login name refers only to alias and not to the whole email address. |
Kerberos/GSSAPI/SSO section
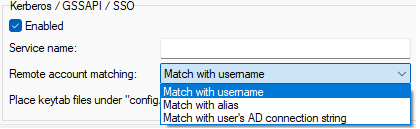
Figure. Directory Service tab: Kerberos/GSSAPI/SSO section.
The syncad.dat File
The file path is [install_directory] > config. Besides of tags with self-explanatory names, this file includes ones that need explanation. See the list of tags below.
<USERNAMEFROMADUSERNAME>1</USERNAMEFROMADUSERNAME> - if enabled (1), account name is imported from attributes givenname and sn, but only in the case both are not empty and vCard synchronization is disabled, otherwise the name is determined in a common manner. For more information refer to How AD Sync Determines User Full Name.
<ALLDATADELETION>0</ALLDATADELETION> - if enabled (1), emails and all other account bound data stored on mail storage are deleted when sync mechanism removes an account from IceWarp Server . This setting prevents accidental data loss (not all of them). On the other hand, it comes at a price as the mail storage has to be purged manually.
<VCARDMAP> - feature that allows control over import of LDIF attributes to IceWarp groupware. For more information refer to vCard Map Feature.
<GROUPSUPPORTREMOTEMEMBERS>0</GROUPSUPPORTREMOTEMEMBERS> - if enabled (1), groups can contain even members whose mail attribute value does not match sync settings (such members would not be accepted as users due to an email address from a different domain). If you want to synchronize a distribution group with email addresses that do not belong to any user synced to IceWarp, this is the option to allow it.
Hierarchical Address Book (HAB)
Synchronization can be configured to convert organization units on the directory server into IceWarp Server groups. These groups can then be a part of HAB. This functionality has to be set manually in the syncad.dat file ([install_directory]/config/).
There are three nodes to configure:
- <CREATEGROUPSFOROUS>1</CREATEGROUPSFOROUS>
This makes the AD/LDAP sync to create groups for all relevant organization units.
For instance, you want to import the following user into IceWarp: dn: CN=Lukas Novak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in. In this case four groups are created automatically: Client, Webmail, Devel and Contacts. Lukas is a member of the Client group. Client group is a member of the Webmail group, etc. The Contacts folder is automatically set as the root group.
Note: The alias of the group has to be plain ASCII and unique. In the order to follow this rule, group aliases are constructed as ou=<name>_<id>.
- <GROUPSFOROUSROOT>OU=Webmail,OU=Devel</GROUPSFOROUSROOT>
This option allows skipping of some organization units from being converted into groups. You can specify which organization unit (must be in scope of DN) to use as the root one. Only units belonging under that unit will be converted into groups.
On the contrary to the previous example, setting the root group like as follows:
<GROUPSFOROUSROOT>OU=Webmail,OU=Devel</GROUPSFOROUSROOT>
synchronization of the same user object:
dn: CN=Lukas Novak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in
would cause creation of only two groups - Client and Webmail. The Contacts folder will not be set as the root group, because we can determine the name of the root from <GROUPSFOROUSROOT>.
- <GROUPSFOROUSROOTNAME>Some
name</GROUPSFOROUSROOTNAME>
This option can override the default name of the root folder.
Examples (all cases require having CREATEGROUPSFOROUS set to 1):
Settings:
<GROUPSFOROUSROOT>OU=Webmail,OU=Devel</GROUPSFOROUSROOT>
<GROUPSFOROUSROOTNAME>Units</GROUPSFOROUSROOTNAME>
User:
dn: CN=Lukas Dvorak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in
Created groups: Units, Client
Settings:
<GROUPSFOROUSROOT></GROUPSFOROUSROOT>
<GROUPSFOROUSROOTNAME>Units</GROUPSFOROUSROOTNAME>
User:
dn: CN=Lukas Dvorak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in
Created groups: Units, Devel, Webmail, Client.
Settings:
<GROUPSFOROUSROOT></GROUPSFOROUSROOT>
<GROUPSFOROUSROOTNAME></GROUPSFOROUSROOTNAME>
User:
dn: CN=Lukas Dvorak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in
Created groups: Contacts, Devel, Webmail, Client.
Settings:
<GROUPSFOROUSROOT>OU=Devel</GROUPSFOROUSROOT>
<GROUPSFOROUSROOTNAME>Units</GROUPSFOROUSROOTNAME>
User:
dn: CN=Lukas Dvorak,OU=Client,OU=Webmail,OU=Devel,DC=icewarp,DC=in
Created groups: Units, Webmail, Client.