DKIM
DomainKeys Identified Mail (DKIM) creates a domain-level authentication framework for email. It uses public-key technology and DNS record to prove the source and content of a message.
You can find general information about DKIM at http://dkim.org/ and the DKIM FAQs at http://dkim.org/info/dkim-faq.html.
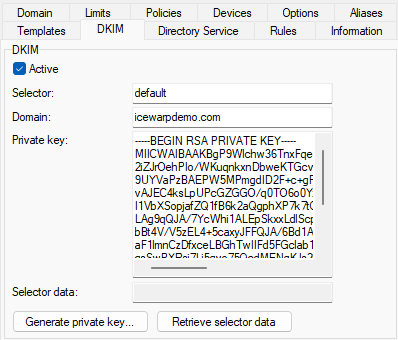
Figure. Domain level management: DKIM tab.
How DKIM works
Sending servers:
- The domain owner generates a public/private key pair. It will be used for signing outgoing messages (multiple key pairs are allowed). The public key is published in a DNS TXT record, and the private key is made available to the DKIM-enabled outbound email server.
- When an authorized user of the email server sends an email, the server uses the private key to generate a digital signature of the message. This digital signature is inserted in the message as a header, and the email is sent as usual.
Receiving servers:
- The receiving email server extracts the signature and tests the domain name and selector for a valid published DKIM record.
- The public key is retrieved from the DNS system for the claimed From: domain. The receiver uses a public key found in the DKIM record in the domain's DNS to decrypt the DKIM signature and authenticate the message.
- The public key is used by the receiving mail system to verify that the signature was generated by the matching private key. A match effectively proves that the email was truly sent from, and with the permission of, the claimed domain and that the message headers and content have not been altered during transit.
- The receiving email system applies local policies based on the results of the signature test. For example, the message might be deleted if the signature does not match.

