Greylisting
Most spammer's servers will try to deliver a message to the receiving server and give up if they do not get a quick response. A "real" server will retry the session after a period of time.
Greylisting allows you to reject an incoming session for a specified period of time. This will deter many spam servers from sending their messages.
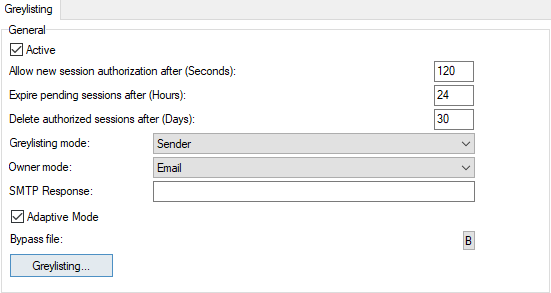
Figure. General section.
Warning: For Greylisting these local bypasses are important:
Bypass trusted IPs
Exclude outgoing messages from spam scanning
Local-local bypass filter
Greylisting bypass file (greylist.dat)
If these are not applied, the users will get a temporary error 4.5.1 in their mail clients and will be allowed to send the message after x seconds.
| Field |
Description |
|---|---|
|
Active |
Check this option to enable Greylisting. |
|
Allow new authorization after (Seconds) |
Specify the amount of time that incoming connections should be rejected. Any retries within this time period will be rejected. |
|
Expire pending sessions after (Hours) |
Specify the amount of time after which any "pending" IP addresses are expired within the database. Note: "Pending" addresses are addresses which have tried to connect and have been rejected by greylisting. |
|
Delete authorized sessions after (Days) |
Specify the number of days that an authorized IP address is held in the database. A value of 0 means authorized IP addresses will never be deleted. Note: "Authorized" addresses are addresses that were rejected by greylisting, but then accepted at a later retry from the address. |
|
Greylisting mode |
Select the data that should be stored in the Greylisting database. There are four possible modes:
Note: The recommended mode is Sender. |
|
Owner mode |
Choose from two options:
|
|
SMTP Response |
If you wish, you can specify a custom SMTP response to be used when a connection is rejected by greylisting. If left blank, the default SMTP response message is returned. |
|
Adaptive Mode |
If enabled, it changes the way how greylisting is applied to senders. When a sender sends an e-mail, classified as a spam, greylisting is turned on for him/her. Hence, his/her next attempts are greylisted. |
|
Bypass file (greylist.dat) |
Click the B button to edit a greylisting Bypass file, where you can specify users, domains and IP address ranges that will not be greylisted. Examples are given within the file. |
|
Greylisting |
Click this button to jump to the Spam Greylist queue. |

